What Is Phishing?
Phishing is a deceptive cyber attack involving fraudulent tactics that manipulate individuals to disclose sensitive information or perform actions that compromise security. Hackers employ various techniques to trick unsuspecting victims, mimicking reputable organizations or individuals to gain their trust.4 Types of Phishing Attacks
There are a wide variety of phishing attacks, including:
1. Email Phishing
Email is the most prevalent form of phishing. Attackers send deceptive emails masquerading as legitimate communications from reputable sources, such as banks, social media platforms, or government agencies. These emails often contain alarming messages that create a sense of urgency, compelling recipients to provide personal information, click on malicious links, or download infected attachments.
2. Spear Phishing
This targeted attack focuses on specific individuals or organizations, tailoring the phishing messages to appear even more legitimate. Attackers gather personal information about their targets to craft personalized emails that deceive recipients into revealing sensitive data or taking malicious actions.
3. Whaling
This form of phishing specifically targets high-profile individuals, such as CEOs or top-level executives. By impersonating trusted contacts or colleagues, hackers aim to deceive these individuals into divulging confidential business information or performing financial transactions.
4. Vishing
Vishing, or voice phishing, involves attackers using voice calls to deceive individuals. They impersonate legitimate entities, such as banks or customer service representatives, and manipulate victims into revealing sensitive information over the phone. These attacks often exploit fear and urgency, creating a sense of immediate action required to deceive the target.
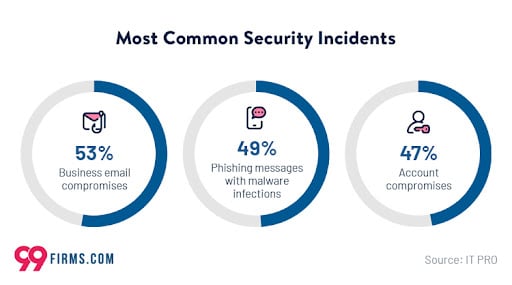
Objectives of Phishing Attacks
A clear objective often drives phishing attacks—attackers seek to exploit sensitive information for personal gain. Let’s take a closer look at some of the primary goals of these attacks:- Personal Identifiable Information (PII) – Includes addresses, names, social security numbers, phone numbers, and other personal information that can be used for identity theft or fraud.
- Financial Credentials – Hackers aim to gain access to banking details, credit card information, and login credentials to carry out unauthorized transactions or commit financial fraud.
- Corporate Data – In targeted attacks on organizations, hackers seek confidential business information, intellectual property, or trade secrets that can be exploited or sold on the black market.
- Credentials for Account Takeover – Some phishing attacks use links or fake login pages to acquire login credentials for various online accounts, including email, social media, e-commerce, or cloud storage platforms. By gaining access to these accounts, attackers can exploit personal information, send fraudulent emails or messages on behalf of the victim, or conduct further phishing attacks.
What Is Smishing?
Smishing, a term derived from “SMS phishing,” is a cyber attack that targets individuals through text messages on their mobile devices. Like phishing, smishing attempts to deceive and manipulate users into performing actions or divulging sensitive information that compromises their security.How Smishing Works
Smishing attacks employ social engineering techniques to exploit human vulnerabilities and elicit immediate responses from unsuspecting victims. Hackers send text messages that appear to be from trusted sources, such as banks, government agencies, or well-known brands, to gain their targets’ trust. These messages often contain urgent or enticing content that prompts recipients to act immediately.Types of Smishing Attacks
There are many types of smishing attacks, including:- Malicious Link Messages: In this type of smishing attack, attackers include a shortened URL in the text message. When recipients click the link, they are redirected to a fake website designed to infect their devices with malware or steal their personal information.
- Prize or Lottery Scams: Fraudsters send smishing messages claiming the recipient has won a prize or lottery. They entice the victims to respond with personal information or pay a fee to claim the prize, leading to potential financial loss or identity theft.
- Financial Scams: Attackers impersonate financial institutions or payment service providers, sending smishing messages that appear authentic. They aim to trick recipients into revealing sensitive banking details, login credentials, or one-time passcodes, which can lead to unauthorized access to accounts and financial fraud.
Urgent or Emergency Messages
This smishing attack preys on people’s emotions by creating a sense of urgency or emergency. The messages might claim that immediate action is required, such as making a payment or revealing personal information to avoid consequences or threats.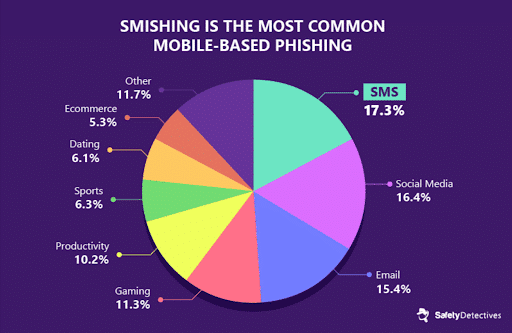
Objectives of Smishing Attacks
Similar to phishing attacks, smishing attacks have clear objectives that hackers seek to achieve:- Financial Gain – Attackers attempt to gain unauthorized access to victims’ bank accounts, credit cards, or other financial information. They may use the obtained data for fraudulent transactions or sell it on the dark web.
- Identity Theft – By tricking individuals into revealing personal information, smishing attacks enable cybercriminals to steal identities and carry out further fraudulent activities.
- Malware Distribution – Clicking on malicious links sent via smishing messages can lead to malware being installed on victims’ devices. Once infected, the hackers can gain control over the device, access personal data, and exploit it for malicious purposes.
Smishing vs. Phishing
Despite their different delivery methods, smishing and phishing attacks have similar objectives and tactics.
Smishing and phishing attacks heavily rely on social engineering tactics to deceive victims and extract sensitive information. Attackers craft convincing messages that exploit emotions and manipulate victims into taking action.
Human vulnerabilities are exploited in these attacks by capitalizing on trust and creating a sense of urgency. Attackers impersonate trusted entities and manipulate victims into divulging information or clicking on malicious links.
Both attacks can target both individuals and organizations. Individuals are targeted through personal devices, while organizations may face more sophisticated and targeted campaigns.
Finally, the main objective of both attacks is to gain unauthorized access to personal or confidential data. This data includes login credentials, financial details, PII, or corporate data, which can be used for malicious purposes.
While smishing and phishing attacks share these similarities, it’s important to remember that they utilize different attack vectors. Smishing attacks use text messages and mobile devices, exploiting their ubiquity and immediacy. Phishing attacks primarily occur through email or fraudulent websites.
5 Ways to Prevent Smishing and Phishing Attacks
Now that we understand the nature and risks of these cyber attacks, let’s explore how you can protect yourself and your organization from being victimized by smishing and phishing attacks. Here are some key prevention measures:
- Be vigilant and skeptical – Exercise caution when receiving messages or emails, especially those requesting personal information or urging immediate action. Verify the sender’s identity before responding or clicking on any links.
- Enable Two-Factor Authentication (2FA) – Implement 2FA for all your online accounts to add an extra security layer beyond passwords.
- Educate yourself and your employees – Invest in comprehensive cybersecurity awareness training, such as CybeReady’s phishing simulation training, to educate individuals about smishing and phishing attacks, their risks, and prevention strategies. By educating yourself and your employees, you can build a culture of cybersecurity awareness and empower everyone to identify and respond to potential threats effectively.
- Keep your devices and software updated – Regularly update your mobile devices and applications to ensure you have the latest security against potential vulnerabilities.
- Use Antivirus and Anti-Malware Software – Install reputable antivirus and anti-malware software on your devices and update them regularly. These tools can detect and block malicious software, including malware distributed through smishing and phishing attacks.
Equip Your Team With Tools to Counter Smishing
In a world where cyber threats continue to evolve and grow, staying informed and taking proactive steps to protect yourself and your organization is crucial. By understanding the risks of smishing and phishing attacks, implementing preventive measures, and fostering a culture of cybersecurity awareness, you can significantly enhance your defenses against these malicious tactics.
As an industry leader in cybersecurity training, CybeReady offers comprehensive solutions to enhance your organization’s security posture. Our phishing simulation training empowers employees with the knowledge and skills to effectively identify and mitigate smishing and phishing attacks. Don’t let these attacks compromise your security and reputation.
Take action today by requesting a demo from Φirki Intelligence to add an extra layer of security to your defenses and stay one step ahead of cyber threats.
