Between May 2023 and May 2024, phishing attacks that target government agencies surged by 360%, with vendor email compromise attacks that mimic trusted third parties more than doubling. In addition, 69% of local government organizations report that they were hit by ransomware in 2023, for which phishing attacks are the most common initial access vector.
It’s clear that government agencies are becoming some of the most lucrative targets for cybercriminals. Read on to understand why, and to learn what organizations can do to protect themselves and their data.
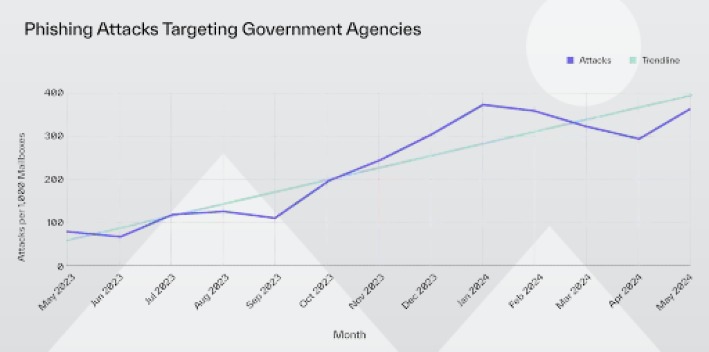
Why is Local Government a Growing Target for Attackers?
Whether you’re a ransomware group looking for a payday, a nation-state hacker thinking about maximum disruption, or a hacktivist aiming to send a political message — the government is a powerful target towards which to aim a cyber attack. When these kinds of attacks are successful, they can bring down critical infrastructure like water and sewage utilities, disrupt public services from education to traffic lights, create opportunities for espionage, or undermine confidence in national security and governance as a whole.
However, despite the risk, government agencies are known to be under-resourced, as well as to work with a complex tech stack of legacy tools. Lean security teams often struggle to keep their heads above water as cyber-attacks become more sophisticated and prevalent, and security training for a wider employee base is often something that falls by the wayside. Pair this with unique legacy infrastructure challenges for each agency, slow approvals processes for modernization initiatives, and a wealth of sensitive data up for grabs — and you can see why government targets are grabbing threat actors’ attention.
Protecting your organization is more crucial than ever, especially as agencies regularly experience double and even triple extortion techniques from ransomware attacks. According to Forbes, 76% of state and local municipalities who were hit by a ransomware attack reported that their data was encrypted, and 48% of victims said the data was stolen — which is the highest rate seen across all industries. The FBI warns that state and local governments are also at high risk of being hit by dual ransomware — a phenomenon where a victim organization is hit again quickly after their first attack by a separate strain of malware or ransomware.
Examples of Cyber Attacks Against State and Local Govt in 2024
Here are just a handful of examples of attacks against government targets over the past few months:
- Miami, U.S., August 2024: A cyber attack against public services shuts down digital systems used by the police and City Hall. Florida law forbids paying the ransom.
- Virginia County, U.S., August 2024: Officials hit by malware disguised as Freedom of Information Act requests.
- Missouri, U.S., April 2024: An attack on weather and transport systems in Kansas took down traffic information including cameras during a dangerous storm.
- Multiple agencies in France, March 2024: Several French government agencies hit by a series of DDoS attacks, with many ministerial services targeted.
- Leicester City Council, UK, March 2024: A ransomware attack took down critical services including energy, social care, and child protective services.
- Colorado, U.S., February 2024: A cyber attack against public defenders leaked information and caused a backlog of cases across the State.
Protecting Public Companies Through Security Awareness Training
While the impact of threat actors targeting state and local governments can be catastrophic, there are ways to reduce the likelihood of an attack and to create a culture of security awareness across your organization. One of the most powerful ways to protect your public company is by reducing your exposure to phishing attacks in the first place. According to Deloitte research, 91% of all cyber attacks start with a phishing email. In state and local government, where information is often publicly available or can be requested under disclosure mandates, attackers can leverage this information to craft even more convincing emails to gain initial access, making phishing even more of a concern.
The FBI provides clear advice in response to the risk of phishing that targets local government and public services. They advise that organizations “implement a user training program and phishing exercises to raise awareness among users about the risks of visiting suspicious websites, clicking on suspicious links, and opening suspicious attachments. Reinforce the appropriate user response to phishing and spearphishing emails.”
At CybeReady, we recognize that security leaders at governmental organizations are stretched thinly, and are often working with lean budgets and security teams. Despite having full responsibility, a CISO can’t have eyes everywhere. We would argue that security awareness training must focus on learning-by-doing, and make sure that simulations are transformed into habits. It’s time to move beyond awareness and into behavioral change.
Working autonomously behind the scenes, our SaaS platform provides a continuous and complete awareness training program for all of your employees, one that can be specifically targeted toward the customized risks of state and local government. It provides a powerful combination of risk reduction, employee engagement, and cultural impact. By demonstrating measurable results through the data gathered by our simulations, employees can feel empowered towards taking accountability for security, and your organization can strengthen itself against the #1 cause of the attack