Android malware ‘FakeCalls’ is circulating again in South Korea, imitating phone calls for over 20 financial organizations and attempting to fool bankers into giving away their credit card details.
The particular malware isn’t new, as Kaspersky published a report about it a year ago. However, Check Point researchers now report that more recent versions have implemented multiple evasion mechanisms not seen in previous samples.
“We discovered more than 2500 samples of the FakeCalls malware that used a variety of combinations of mimicked financial organizations and implemented anti-analysis techniques,” reads CheckPoint’s report.
“The malware developers paid special attention to the protection of their malware, using several unique evasions that we had not previously seen in the wild.”
Voice phishing
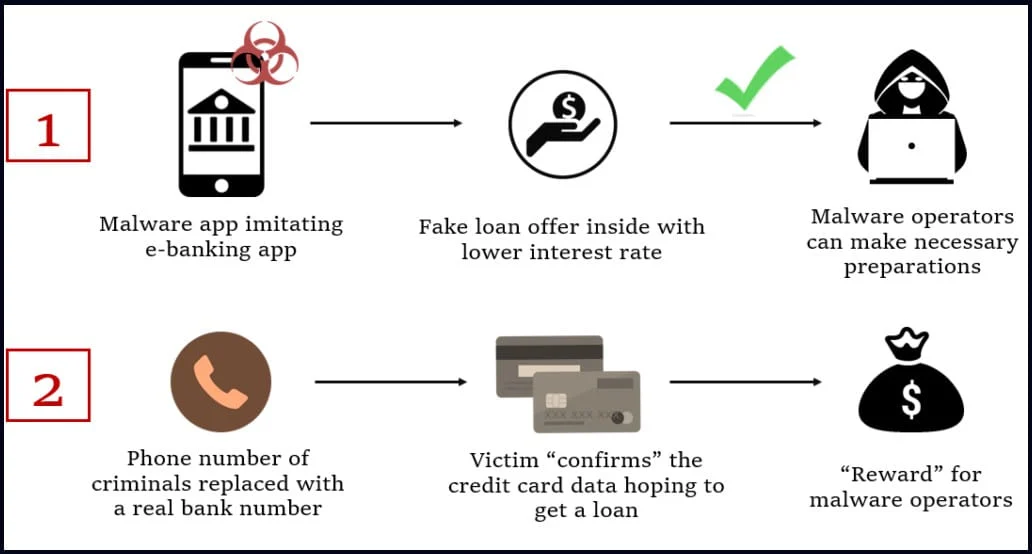
The first step of the attack is the installation of malware on the victim’s device, which might happen via phishing, black SEO, or malvertizing.
The FakeCalls malware is distributed on fake banking apps that impersonate large financial institutions in Korea, so victims think they are using a legitimate app from a trustworthy vendor.
The attack begins with the app offering the target a loan with a low-interest rate. Once the victim is interested, the malware initiates a phone call that plays a recording from the bank’s real customer support with instructions on getting the loan request approved.
However, the malware can mask the called number, which belongs to the attackers, and instead displays the impersonated bank’s real number, making the conversation appear realistic.
At some point, the victim is tricked into confirming their credit card details, supposedly required for receiving the loan, which are then stolen by the attackers.
 Android FakeCalls attack diagram (CheckPoint)
Android FakeCalls attack diagram (CheckPoint)
In addition to the vishing process, FakeCalls can capture live audio and video streams from the compromised device, which could help the attackers collect additional information.
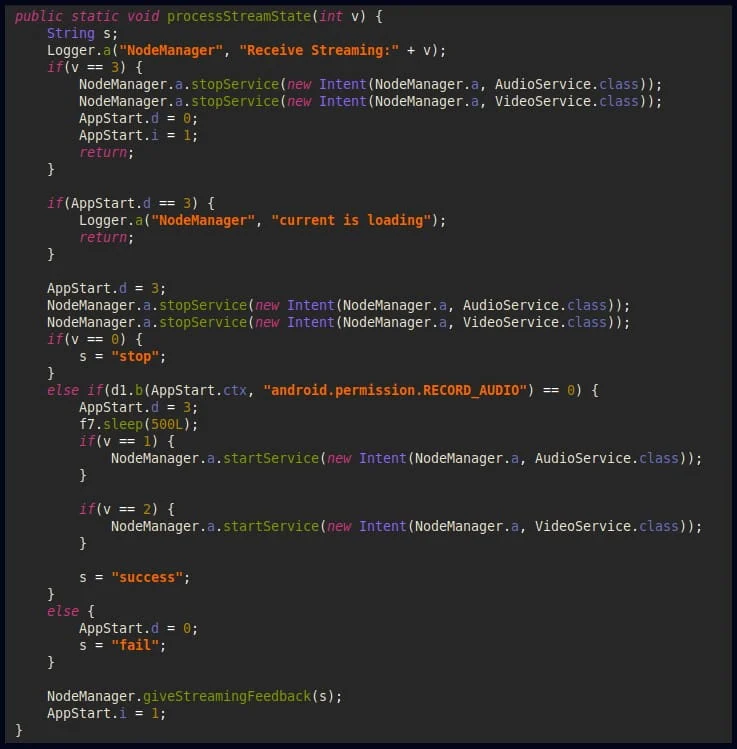
Android fake app Code to initiate live stream (CheckPoint)
Evading detection
In the latest samples captured and analyzed by CheckPoint’s researchers, FakeCalls incorporates three new techniques that help it evade detection.
The first mechanism is called ‘multi-disk,’ which involves manipulating the ZIP header data of the APK (Android package) file, setting abnormally high values for the EOCD record to confuse automated analysis tools.
The second evasion technique involves the manipulation of the AndroidManifest.xml file to make its starting marker indistinguishable, modify the strings and styles structure, and tamper with the last string’s offset to cause incorrect interpretation.
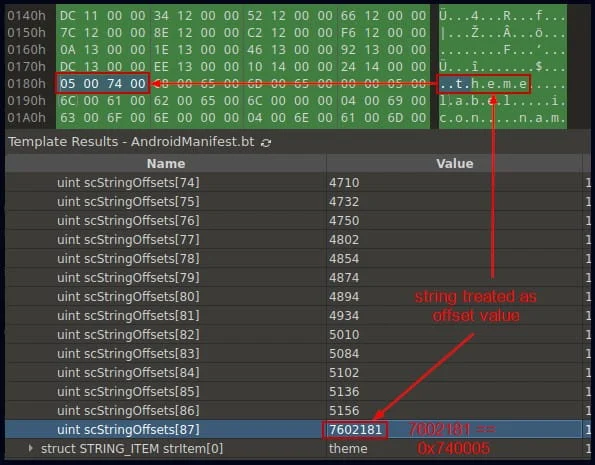
Android fake app Wrong last string offset in the array (CheckPoint)
Finally, the third evasion method is to add many files inside nested directories in the APK’s asset folder, resulting in file names and paths surpassing 300 characters. Check Point says this can cause problems for some security tools, causing them to fail to detect the malware.
 Android fake app Files in the APK asset folder (CheckPoint)
Android fake app Files in the APK asset folder (CheckPoint)
A costly problem
According to South Korean government stats, vishing (voice phishing) is a problem that has cost victims in the country $600 million in 2020 alone, while there have been 170,000 reported victims between 2016 and 2020.
While FakeCalls has stayed in South Korea, the malware could easily expand its operations to other regions if its developers or affiliates develop a new language kit and app overlay to target banks in different countries.
Vishing has always been a dire problem, but the rise of machine-learning speech models that can generate natural speech and mimic real persons’ voices with minimal training data input is poised to magnify the threat shortly.
