Android malware ‘FakeCalls’ is circulating again in South Korea, imitating phone calls for over 20 financial organizations and attempting to fool bankers into giving away their credit card details. The
Category: Blog
Cynet Security Achieves 426% ROI in Forrester Total Economic Impact™ StudyCynet Security Achieves 426% ROI in Forrester Total Economic Impact™ Study
Cost savings and business benefits were quantified in “The Total Economic Impact™ of Cynet All-in-One Security,” a commissioned study conducted by Forrester Consulting on behalf of Cynet in October 2024. The

Understanding PCI DSS and the New PCI DSS 4.0: Comprehensive Guide and Key RequirementsUnderstanding PCI DSS and the New PCI DSS 4.0: Comprehensive Guide and Key Requirements
The Payment Card Industry Data Security Standard (PCI DSS) is a globally recognized framework developed to ensure the security of card transactions and protect cardholder data from breaches, fraud, and

Understanding Cybersecurity Regulation: A Comprehensive OverviewUnderstanding Cybersecurity Regulation: A Comprehensive Overview
As the world becomes increasingly dependent on digital systems, the need for robust cybersecurity frameworks has never been more pressing. Cybersecurity regulation refers to the set of legal, technical, and
AI and Cybersecurity Jobs: Evolution or Replacement?AI and Cybersecurity Jobs: Evolution or Replacement?
As artificial intelligence (AI) continues to advance, the question of whether it will replace cybersecurity jobs is gaining traction. With the power to analyze vast datasets, detect anomalies, and automate

Understanding Penetration Testing vs. Automated Penetration TestingUnderstanding Penetration Testing vs. Automated Penetration Testing
Key Differences, Similarities, Pros, and Cons What is Penetration Testing? Penetration testing, commonly referred to as a “pen test,” is a simulated cyberattack on a computer system, network, or web

Bridging the Security Gap: How a Virtual CISO Empowers Businesses of All Sizes with Remote and Scalable ExpertiseBridging the Security Gap: How a Virtual CISO Empowers Businesses of All Sizes with Remote and Scalable Expertise
What is a vCISO? A Virtual Chief Information Security Officer (vCISO) is a remote, outsourced professional who offers cybersecurity expertise and strategic guidance to organizations. Unlike a traditional CISO, a
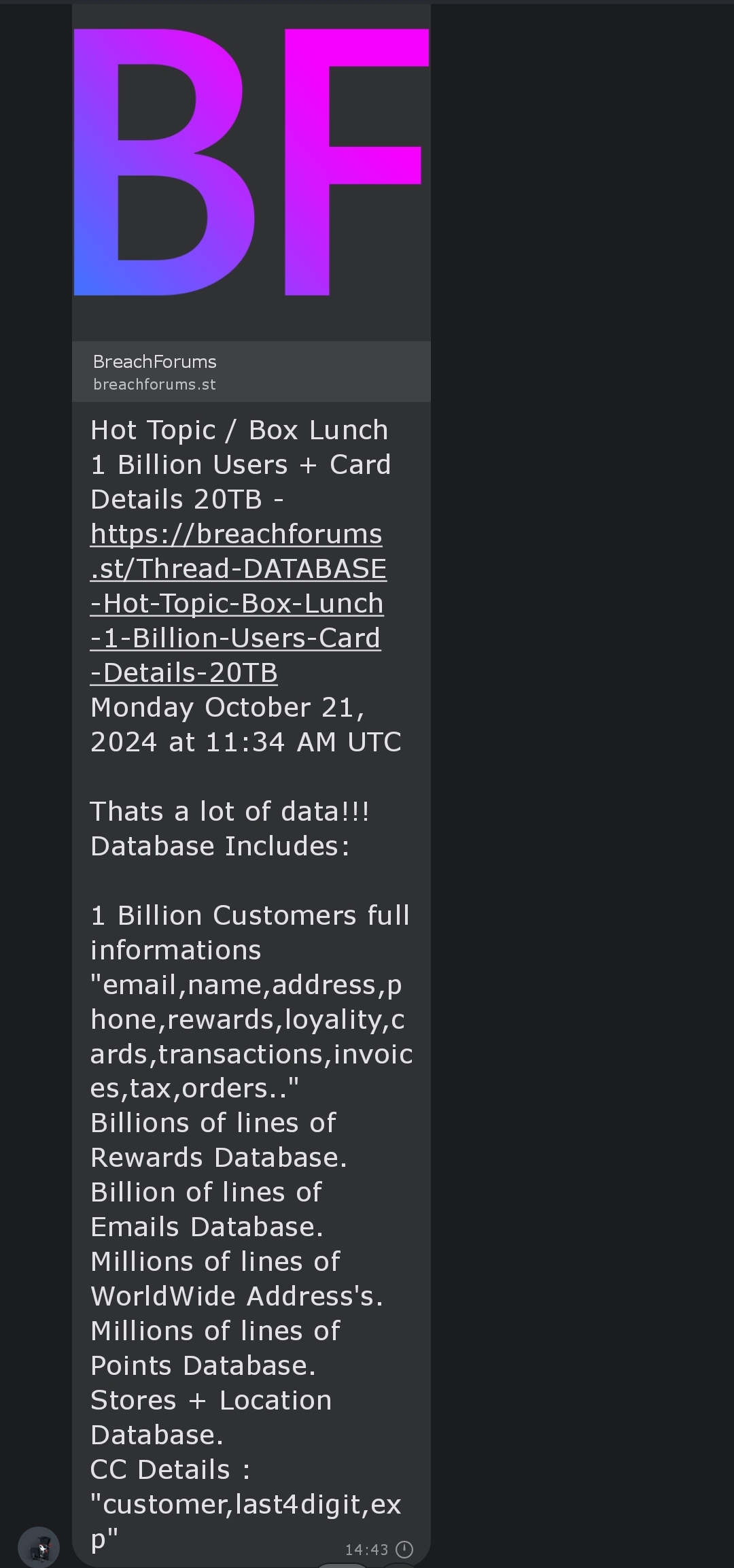
Breaking News! Box Lunch Data BreachBreaking News! Box Lunch Data Breach
Hot Topic / Box Lunch 1 Billion Users + Card Details 20TB – https://breachforums.st/Thread-DATABASE-Hot-Topic-Box-Lunch-1-Billion-Users-Card-Details-20TB Monday October 21, 2024 at 11:34 AM UTC Thats a lot of data!!! Database Includes: 1 Billion

Ransomware Report: Unveiling Trends in Attack Payouts and NegotiationsRansomware Report: Unveiling Trends in Attack Payouts and Negotiations
Ransomware attacks represent a significant cybersecurity threat, affecting various sectors and individuals. This study examines a comprehensive dataset of ransomware payments and chat logs to better understand the strategies and
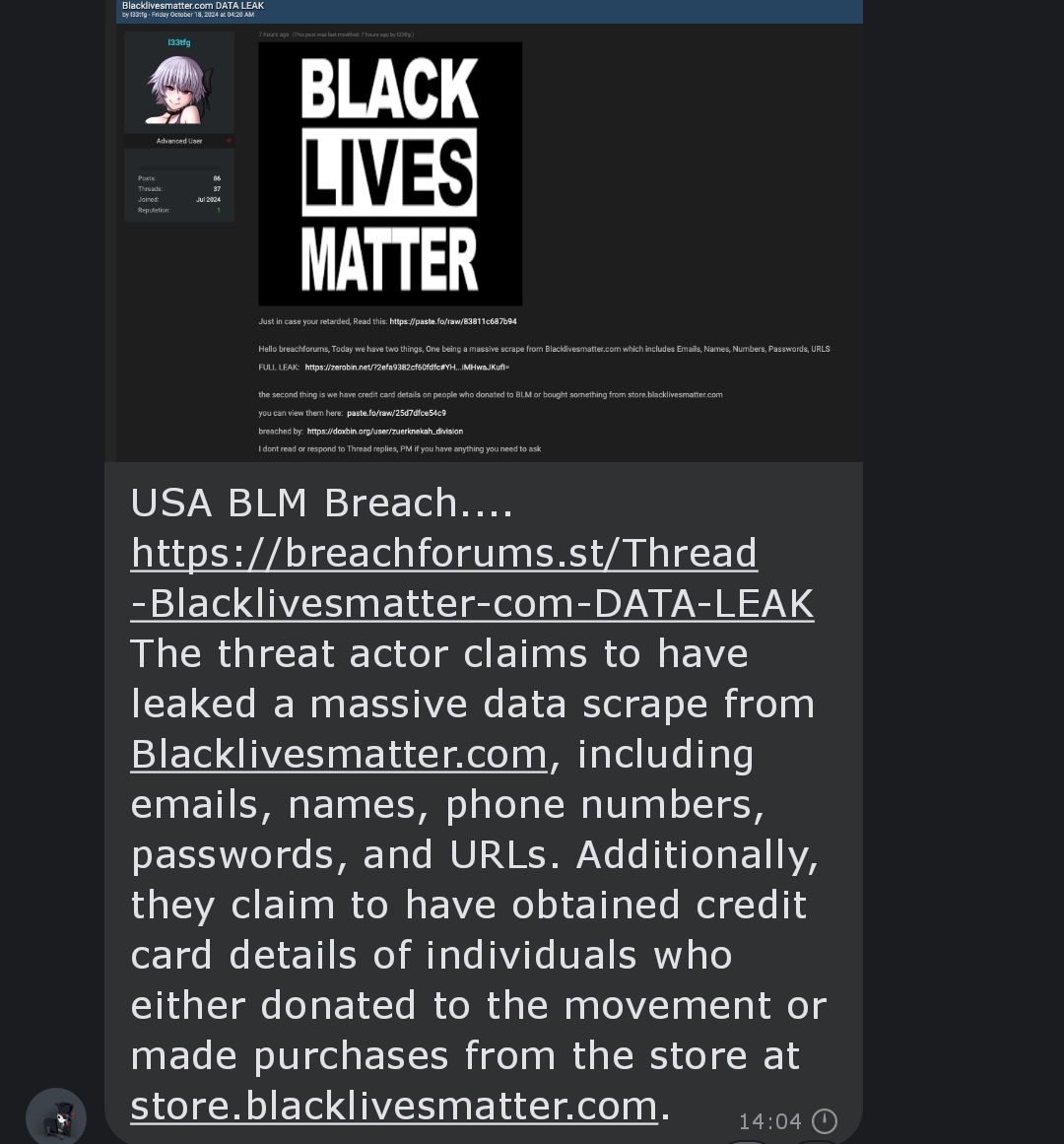
Breaking News! Black Lives Matter Data LeakageBreaking News! Black Lives Matter Data Leakage
The threat actor known as “l33tfg” seems to have leaked data belonging to Black Lives Matter, from the store at http://store.blacklivesmatter.com What Are Breach Forums All About? BreachForums, sometimes referred to as Breached,
